Amiibo
Amiibo are NFC figures made by Nintendo, used in games in different forms (different in each game). It can be used with the New3DS and the Old3DS with an IR peripheral.
Tag information
- Model: NTAG215
- Manufacturer: NXP Semiconductor
- Page size: 4 bytes
- Page count: 135 pages (540 bytes)
- Data pages: 126 pages (504 bytes)
Page layout
Excluiding the configuration pages at the end, the structure of the NFC pages is as following:
| NFC page | Total pages | Raw byte offset in EEPROM | Total byte size | Writable | Description |
|---|---|---|---|---|---|
| 0x0 | 0x4 | 0x10 | 0x10 | No | Same as standard NTAG215: 9-byte serial-number, "internal" u8 value, two lock bytes then the "Capability Container (CC)" page. |
| 0x4 | 0x1 | 0x10 | 0x4 | Yes | Last 3-bytes here are used with the following HMAC where the size is 0x1DF-bytes. The u16 starting at byte1 is used for the first two bytes in the 0x40-byte input buffer for Amiibo crypto init. The first byte is normally 0xA5. The remaining bytes are initially(before the Amiibo is written to) all-zero. Byte[2](maybe big-endian u16 starting at byte1?) here is incremented each time the Amiibo is written to. |
| 0x5 | 0x8 | 0x14 | 0x20 | Yes | The system crypts 0x1A0-bytes with some data from here, see below. |
| 0xD | 0x8 | 0x34 | 0x20 | No | SHA256-(HMAC?) hash. The first 0x18-bytes of this hash is section3 in the encrypted buffer. |
| 0x15 | 0xB | 0x54 | 0x2C | No | This is plaintext data, see below. |
| 0x20 | 0x8 | 0x80 | 0x20 | Yes | SHA256-(HMAC?) hash over 0x1DF-bytes: first 3-bytes are from the last 3-bytes of page[4], the rest is over the first 0x1DC-bytes of the plaintext data. |
| 0x28 | 0x45 | 0xA0 | 0x114 | Yes | This is section1 in the encrypted buffer. |
| 0x6D | 0x15 | 0x1B4 | 0x54 | Yes | This is section2 in the encrypted buffer. |
Specifications can be found on this image, which is a compilation of screenshots made by scanning a Samus amiibo with the Android App "NFC TagInfo":
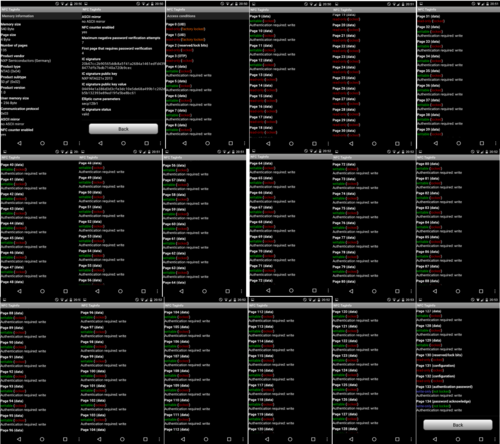
See here regarding the Amiibo encryption.
Data structures
Structure of the data starting at page 0x15
| Offset | Size | Description |
|---|---|---|
| 0x0 | 0xC | ? |
| 0xC | 0x20 | Probably a SHA256-HMAC hash. |
Encrypted data buffer structure
| Encrypted buffer offset | Raw byte offset in NFC EEPROM | NFC page | Byte size | Notes |
|---|---|---|---|---|
| 0x0 | 0x14 | 0x5 | 0x20 | |
| 0x20 | 0xA0 | 0x28 | 0x114 | |
| 0x134 | 0x1B4 | 0x6D | 0x54 | |
| 0x188 | 0x34 | 0xD | 0x18 | This data is included in the crypto buffer, even though this data isn't actually encrypted(this is part of a hash). |
Structure of the plaintext data
| Offset | Size | Description |
|---|---|---|
| 0x0 | 0xB0 | Amiibo settings are stored within here. |
| 0xB0 | 0xD8 | AppData, for the user-application specified in the above Amiibo settings. The data stored here is application-specific. |
| 0x188 | 0x18 | Not used in "decrypted" form, since this isn't encrypted to begin with. |
Structure of Amiibo settings
| Offset | Size | Description |
|---|---|---|
| 0x0 | 0x1 | Flags. The low 4-bits here are copied to the struct used with NFC:GetAmiiboSettings. The below setup date is only loaded when bit4 and/or bit5 here are set, otherwise value 0 is used instead for the date. Bit4=1 indicates that the Amiibo was setup with amiibo Settings: NFC:GetAmiiboSettings will return an all-zero struct when this is not set.
Bit5=1 indicates that the AppData was initialized. NFC:InitializeWriteAppData will return an error if this is value 1, when successful that command will then set this bit to value 1. |
| 0x1 | 0x1 | Unknown. The low 4-bits here are copied to the struct used with NFC:GetAmiiboSettings. |
| 0x2 | 0x2 | This big-endian u16 counter is incremented each time that the CRC32 at offset 0x8 gets updated by NFC:InitializeWriteAppData, due to that value not matching the calculated one. When this value is already 0xFFFF, this counter won't be updated anymore. |
| 0x4 | 0x2 | u16 big-endian date value, see below. This is the date for when the Amiibo was initially setup in amiibo Settings. This is also written by NFC:InitializeWriteAppData. |
| 0x6 | 0x2 | u16 big-endian date value, see below. This is the date for when the Amiibo was last written to. |
| 0x8 | 0x4 | Big-endian CRC32 value with initialval=~0, with the 8-byte output from Cfg:GenHashConsoleUnique. This is written by NFC:InitializeWriteAppData, when the current value doesn't match the calculated one. |
| 0xC | 0x14(10*2) | UTF-16BE Amiibo nickname. |
| 0x20 | 0x60 | Owner Mii. |
| 0x80 | 0x8 | Big-endian application programID/titleID from the application which initialized the AppData, zero otherwise. This is only written, not compared with the user application titleID: doing the latter would break games' cross-platform compatibility with 3DS<>Wii U(Super Smash Bros 3DS/Wii U for example). |
| 0x88 | 0x2 | u16 big-endian. This value is incremented each time the Amiibo is written to. When this value is already 0xFFFF, this counter won't be updated anymore. |
| 0x8A | 0x4 | Big-endian u32 Amiibo AppID. |
| 0x8E | 0x2 | ? |
| 0x90 | 0x20 | Probably a SHA256-HMAC hash. |
Format of the big-endian date values:
| Bit | Description |
|---|---|
| 0-4 | Day |
| 5-8 | Month |
| 9-15 | Year, relative to 2000. |
3DS read/write procedure
Note this is the procedure used by the console, but isn't the only way of reading them.
Read procedure
- GET_VERSION
- READ, startpage=0x03. The read page data for page[0x3] must match little-endian 0xEEFF10F1.
- PWD_AUTH. Key is based on UID.
- FAST_READ: startpage=0x00, endpage=0x3B
- FAST_READ: startpage=0x3C, endpage=0x77
- FAST_READ: startpage=0x78, endpage=0x86
Therefore, *all* pages from the Amiibo NFC tag are read, including the configuration pages at the end.
Write procedure
- GET_VERSION
- READ, startpage=0x03. The read page data for page[0x3] must match little-endian 0xEEFF10F1.
- PWD_AUTH. Key is based on UID.
- Multiple WRITE commands for writing to pages 0x04..0x0C. The first byte for page[4] is zero here.
- Multiple WRITE commands for writing to pages 0x20..0x81.
- Use the last 3 commands from the above reading section.
- WRITE: page=0x04, same data as before except first byte is 0xA5 this time.
- FAST_READ: startpage=0x04, endpage=0x04